You can restore your SQL server database after ransomeware attack through- restoring data from backups, using system restore, extracting files from emails, search for contact and emails, or through a database recovery software.
In this article, we’ll dig a little deeper on these methods to learn how you can restore SQL database files after a ransomware attack. But before that – we’ll have a quick look at Ransomware, and what it does to your files.
Content-
1. What is Ransomware
2. Methods to Restore SQL Database
3. Key Takeaways
Ransomware in Brief-
Ransomware is a malware application that encrypts important databases files, and thereby denying users from access to their files. It then asks for a ‘ransom’ from users for access to the inaccessible files.
Here’s what Kaspersky has to say about Ransomware:
“Ransomware is malicious software that infects your computer and displays messages demanding a fee to be paid in order for your system to work again. This class of malware is a criminal moneymaking scheme that can be installed through deceptive links in an email message, instant message or website. It has the ability to lock a computer screen or encrypt important, predetermined files with a password.”
In other words, ransomware is an application that encrypts user data; and then takes a payment for access to these files.
Work of the devil.
It is suffice to say that paying the ransom is out of question. Why? Because there is no certainity that your data will be decrypted, or that it will not happen again in the future.
Methods to Restore SQL Server Database After Ransomware Attack-
Ransomware will encrypt each and any file that it finds on a local computer; and unfortunately for database administrators, it includes SQL server files too. In fact, Ransomware attacks on SQL Servers have become increasingly common.
If you are a database administrator whose files have been encrypted by malware, do not fear. In my research for this article, I’ve come up with the best methods to restore SQL server database after a ransomware attack-
Method #1: Restore SQL Server Database From a Previous Backup-
You can restore SQL Server Database from a previous backup. In many cases, it method should solve the problem. There is, however, a catch.
This will only work if you have the database before hand, i.e., before the encryption. Makes sense. Also, the backup itself should be uncorrupted or unencrypted. Furthermore, in-spite of having the backup, all changes performed after the backup will be lost. So there’s that too.
Method #2: Use System Restore-
You can use the system restore method to recover SQL server database files after ransomware attack.
You can perform system restore from control panel. Note that this will take your whole system back, not just the SQL server database, to a previous point in time. All the changes and new data will be lost.
Method #3: Use Enterprise Software-
As you’ve probably realized by now, the methods discussed above might work or they might not. But when you are dealing with huge amounts of important data, you don’t want to take a chance.
In situations such as these, it is recommended to use a professional software like the SysTools SQL Recovery tool. It will automate the recovery process of SQL server database files affected by Ransomware attack. Here’s how you can recover your database:
- Install and launch the SysTools SQL Recovery software.
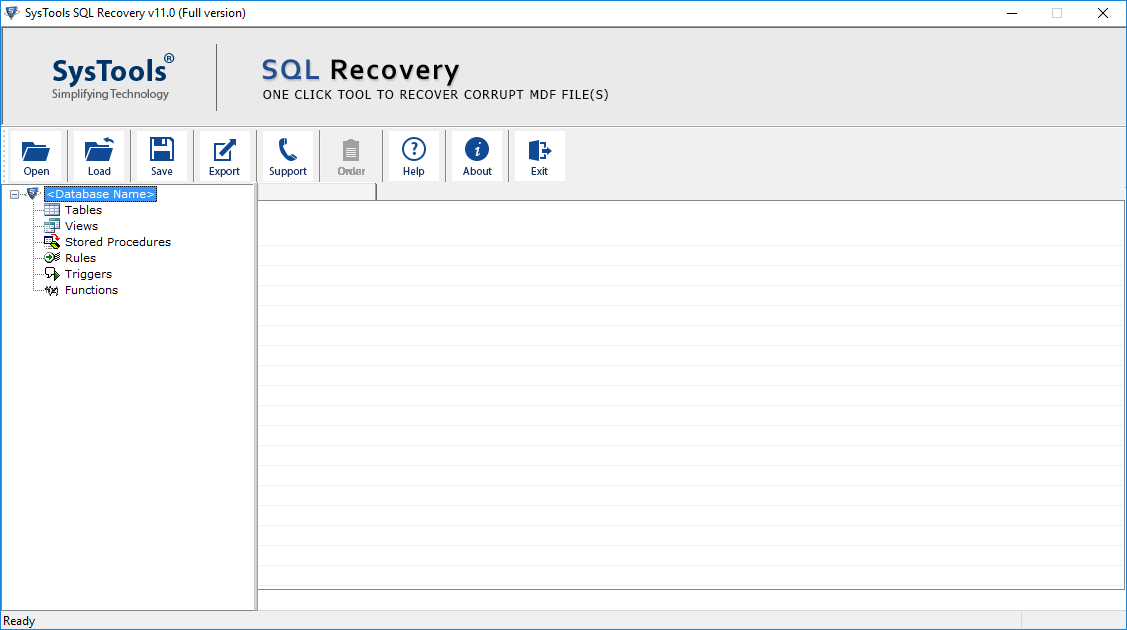
- Click on Open and select the MDF file to recover.
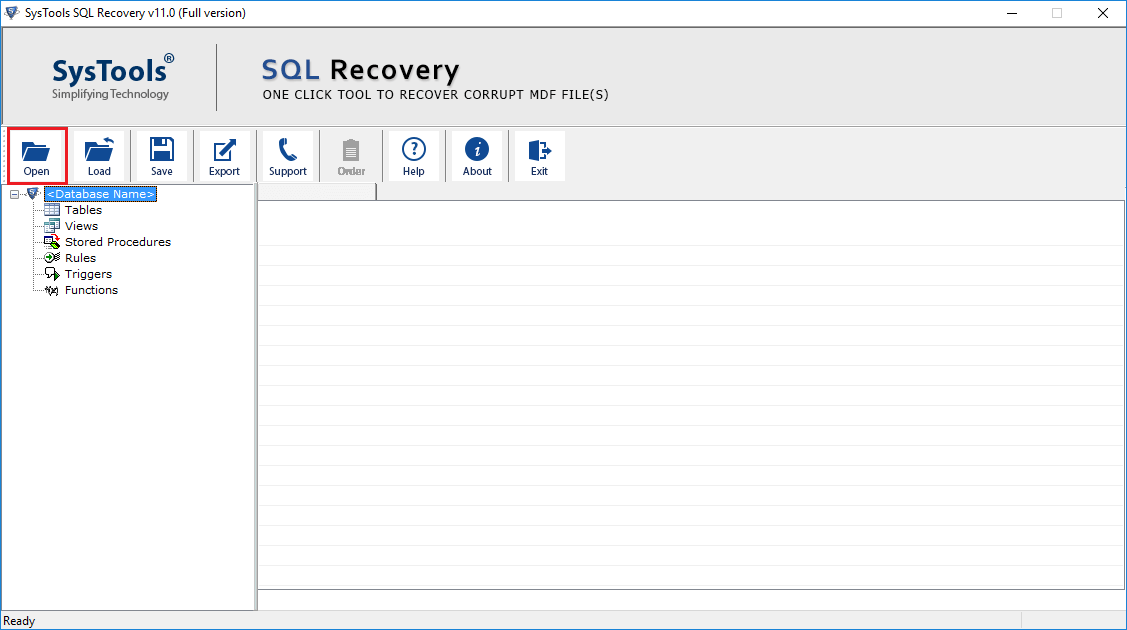
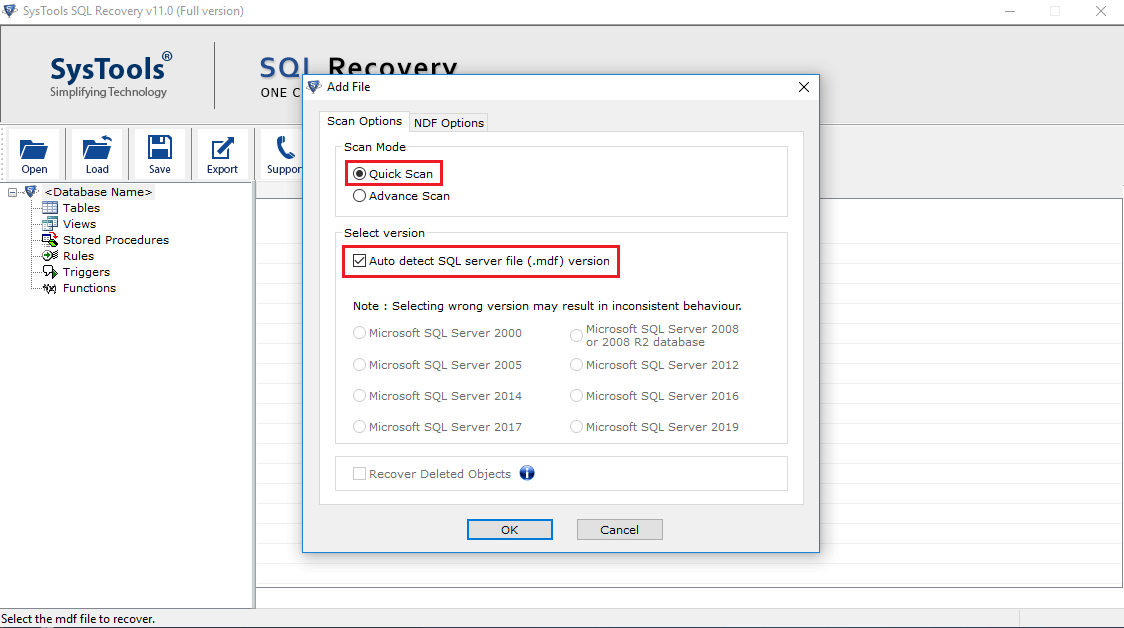
- Chose quick or advanced scan and check the Autodetect MDF version radio button.
- Click on OK. This will give you a preview of the recovered files.
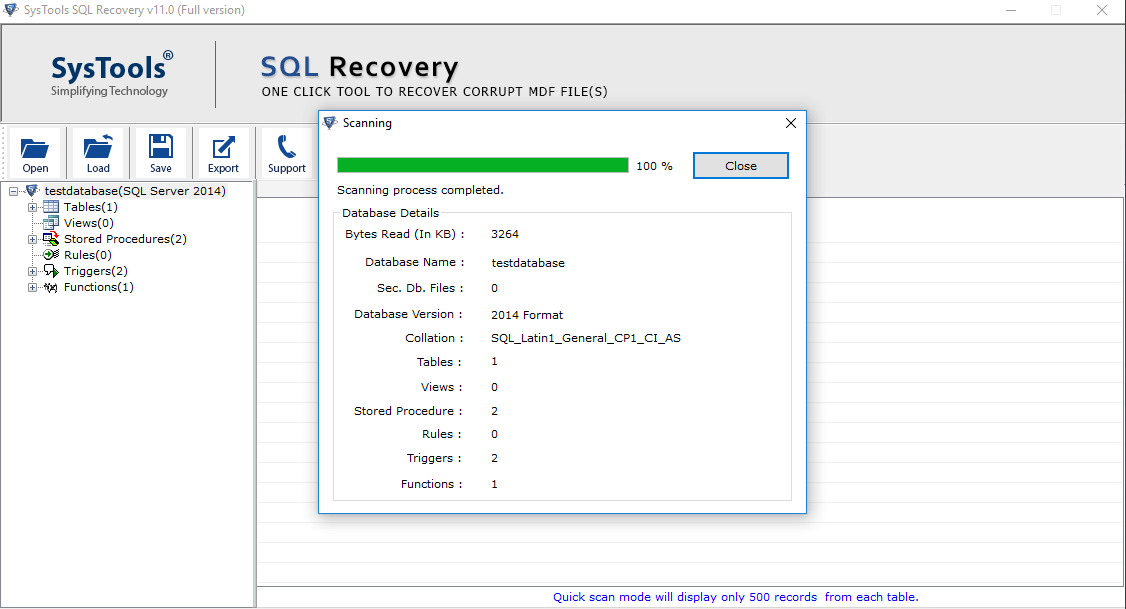
- You can preview the database objects like tables, views, stored procedures, etc.
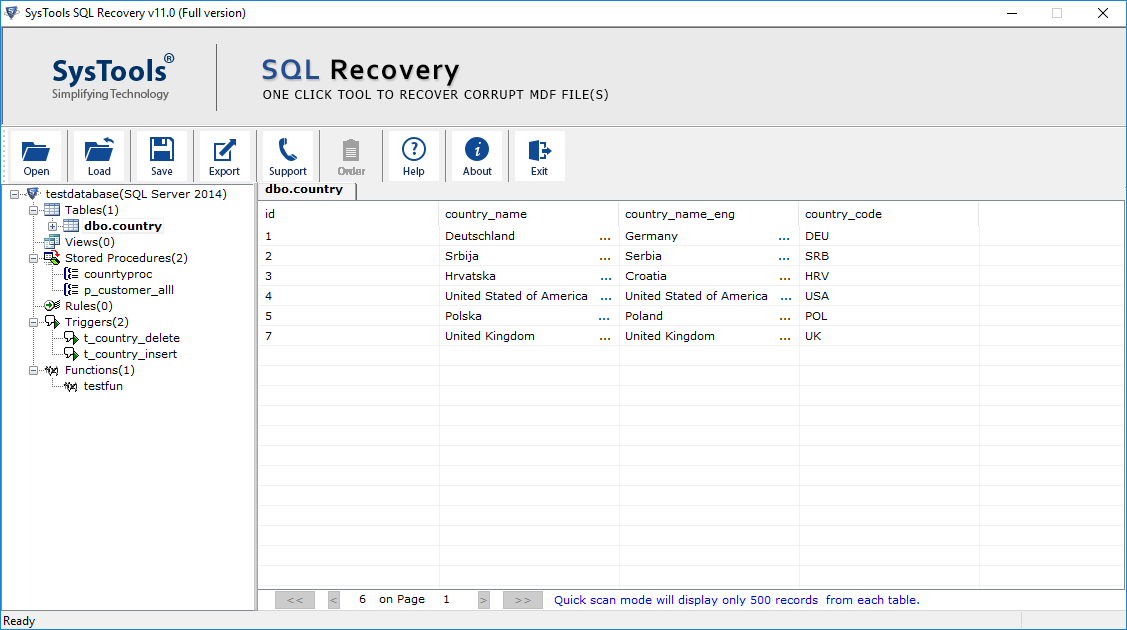
- Now click on Export to recover the data.
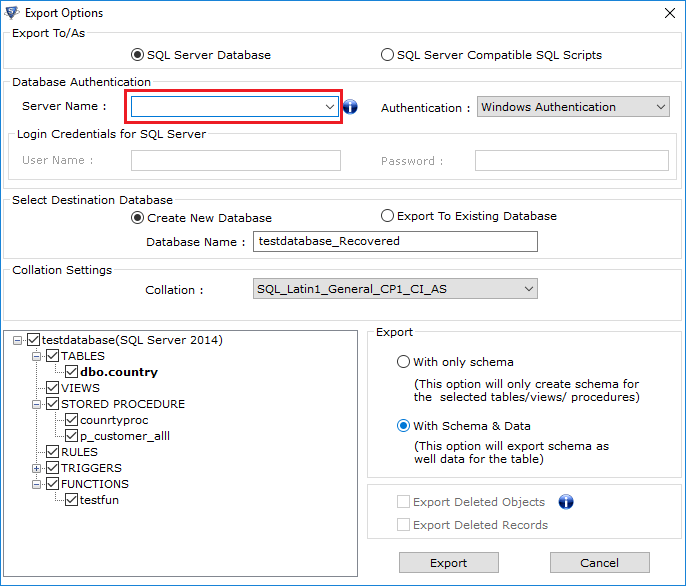
- Here we will Export the data as SQL Server Database.
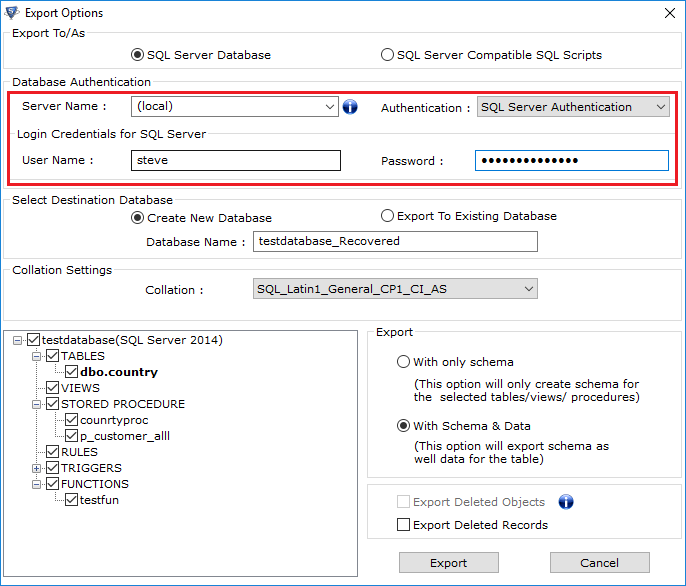
- Fill Server Authentication details like Server Name & choose Authentication type as Windows Authentication or SQL Server Authentication.
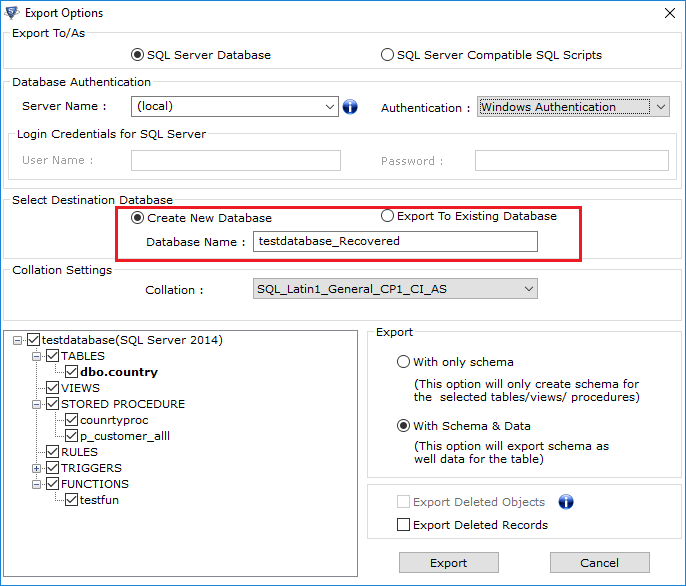
- You have two different options to migrate database objects from one database to another.
- Create New Database
or - Export to Existing database.
- Create New Database
- Create New Database-
- If you choosing to Create New Database option, then you need to give Database Name to a new database.
- Select objects you want to move.
- Choose either of the options: export the MDF file With Only Schema or With Schema & Data.
- If you save the database components (tables/views/Procedures) With Only Schema then the software will export the schema/structure of selected database components
- An ‘Export Completed’ Window will appear on screen confirming the successful export of the database. Click on OK.
- Click on Close. It will ask to export the details in a .csv file. Click on yes to save the report.
- Open the exported .csv file to view exported items.
- The exported records count shows 0 when you export the database objects With Only Schema option.
- Now launch SQL Server again and expand the databases to check newly migrated the database.
- Expand the newly created database to check all the migrated objects (Tables, functions, stored procedures, views, etc.)
- Export to Existing database-
- If you want to migrate the database objects to an existing database then check the Export to Existing Database option.
- Here we have created a new database named as EMPTY to show how to migrate database objects in an existing database.
- Now for ex. let’s migrating a single table dbo.productdetail from SAMPLE database to EMPTY database.
- Checking the available records in dbo.productdetail by executing select statement.
- In database Name, selecting the destination database (EMPTY) to migrate selected or all database objects from the SAMPLE database.
- Now selecting dbo.productdetail for migration.
- Next, Software allows us to migrate data With Only Schema or Schema & Data.
- The software will ask for Export Deleted Records as well. Click on Yes, if you want.
- The Export completed popup will prompt on software screen once the export process completed successfully.
- After clicking on Ok, Software will display the exported database object with record count and Status.
- By Clicking on Close, SQL Server Database Migrator asks for export the details of exported items in .csv file. Click on Yes to save the report.
- Browse the folder to save .csv detail in desired location or software allow you to Make New Folder to save the .csv detail in it.
And just like that, your affected SQL server database files will be recovered in a few clicks.
Key Takeaways-
Ransomware are the Bubonic Plague of internet today. They are on the rise, and are expected to cost a whopping $20 billion, according to Cybersecurity Ventures. Ransomware attacks on SQL Servers are becoming common too.
They are a threat to database administrators like you because they attack and encrypt the MDF files of your SQL server database systems and make them inaccessible; until you pay them a ransom. You can avoid this by using enterprise software like SysTools SQL Recovery that will restore SQL server database files after ransomware attacks.