
By Christos Flessas
In the modern digital age, the role of APIs in the realm of cybersecurity cannot be overstated. As the invisible bridges connecting different applications, APIs facilitate seamless data flow and integration, making them a vital cog in the machinery of today’s interconnected ecosystem. Yet, as their prevalence and importance grow, so do the risks associated with them.
Undoubtedly, cybercrime increases and evolves unprecedentedly nowadays; APIs are at risk. Their popularity, extensive use, and the continuous growth of their financial importance make them vulnerable to bad actors and a lucrative target for cybercriminals. API economy rings the alarm of API security: APIs are paramount, and businesses of any size and sector must take adequate measures to protect them.
APIs are pivotal to contemporary digital ecosystems, enabling interconnectivity and smooth integration between various applications, platforms, and systems. Salt Security highlights the importance of APIs: “They keep everyone connected to vital data and services, enable all sorts of critical business operations, and make digital transformation possible.”
With the rising dominance of API integrations, there’s an urgent impetus to fortify API security. Cybersecurity professionals must comprehend the gravity of this matter, given the sophisticated landscape of threats emerging in parallel. Still not convinced? The following statistical insights underscore the paramount importance of robust API security:
API integrations’ dynamic and intricate landscape has become a fertile ground for cyber adversaries. The statistics mentioned above accentuate the escalating threats and their substantial repercussions. They provide a glimpse into the current state of API security and highlight the urgent need for robust security measures.
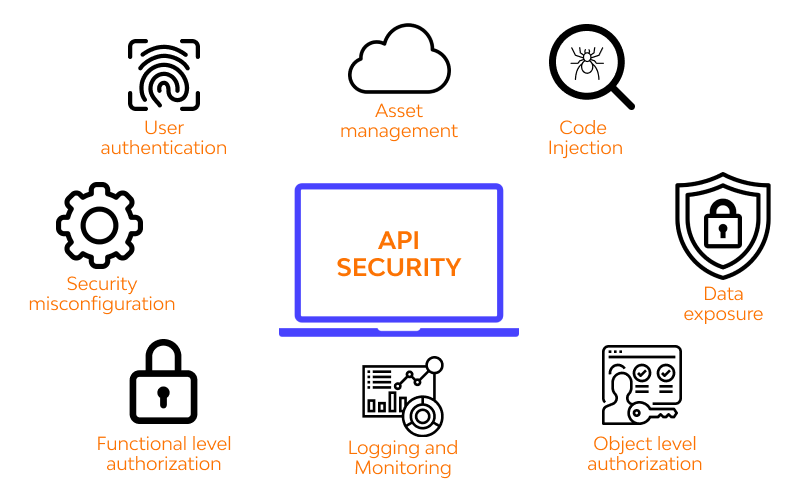
The Open Web Application Security Project (OWASP) has identified the top 10 API security risks for 2023. These risks include authorization and authentication issues, unrestricted access and resource consumption, Server-Side Request Forgery (SSRF) flaws, and improper inventory management. A business shall familiarize itself with these risks to develop effective security strategies.
The exponential rise in API integration correlates with an increased threat surface. As cyber threats evolve, organizations must prioritize API security to protect sensitive data, maintain customer trust, and mitigate financial risks.
Additionally, cybersecurity professionals must take adequate API security measures, leveraging advanced technologies and adhering to regulatory compliances. Regular audits, continuous monitoring, and adoption of best practices are crucial to fend off the encroaching threats and safeguard the organizational digital assets against the burgeoning risks associated with API vulnerabilities.
The API Security vision
The perpetual evolution of the threat landscape commands a proactive and advanced approach, coupled with a strategic vision, to anticipate, combat, and mitigate the multifaceted threats targeting APIs. The collaborative efforts of the cybersecurity community and continual investments in API security will be pivotal in navigating the uncharted territories of the contemporary digital ecosystem.
Remember, a secured API is not just a technological requisite; it’s a strategic asset in fostering innovation and thus cannot be left vulnerable.
About the Author: Christos Flessas is a Communications and Information Systems Engineer with more than 30 years of experience as an Officer of the Hellenic Air Force (HAF). He is an accredited NATO tactical evaluator in the Communication and Information Systems (CIS) area and the National Representative (NatRep) at Signal Intelligence CIS and at Navigation Warfare (NavWar) Wrking Groups. Christos holds an MSc in Guided Weapon Systems from Cranfield University, UK. He has also attended numerous online courses such as the Palo Alto Networks Academy Cybersecurity Foundation course. His experience covers a wide range of assignments including radar maintenance engineer, software developer for airborne radars, IT systems manager and Project Manager implementing major armament contracts.
Christos is intrigued by new challenges, open minded, and excited for exploring the impact of cybersecurity on industrial, critical infrastructure, telecommunications, financial, aviation, and maritime sectors.
The way we consume entertainment has changed dramatically, with Subscription Video on Demand (SVOD) leading…
The Evolution of Inventory Tracking RFID inventory management software is transforming how businesses track, manage,…
The Unexpected Costs of Unprotected Windshields Polaris Ranger windshields protection is more than just a…
Probably one of the best things people do to secure their finances is the purchase…
The iPhone 15 is still a great buy Released in 2023, the iPhone 15 brought…
By Josh Breaker-Rolfe Data security posture management (DSPM) is the rising star of the data…